Benefits
Cybersecurity improves organizations
- Improves internal, external & public confidence
- Enhances IT system robustness & continuity
- Can be a profit center (not cost center)
- Increases functionality & resilience
- Increases efficiency & productivity
- Enables new business initiatives
- Reduce costs & lowers TCO
- Increases ease of use
- Fosters innovation
Security is a Balance
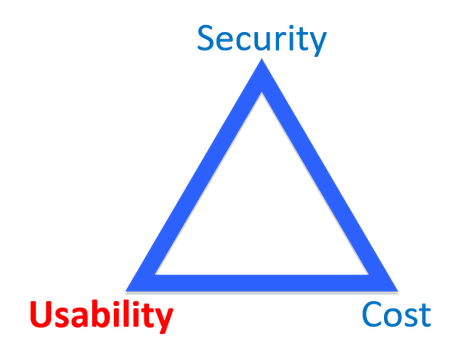
We help you find that balance
Opportunity for change
Cybersecurity is mandatory (so do it effectively)
Core to the integration and implementation of any business strategy
Business and IT alignment
- Opportunity to connect different businesses (silos) together
- Data (cybersecurity) is now central to an organization strategy
- Lower data friction
- Increase efficiency, innovation and business growth
Enhances workforce productivity
- Increases corporate speed, agility, and ROI
- Enhances (not limit) collaboration and productivity by allowing multiple teams to access, scale and analyze data
- Cuts across multiple layers - people, process, platform, and protection
Accelerates cloud migration
- Allows for speed, scale and resilience
- Allow multiple teams to access, scale and analyze data
- Save money and increase security
Holistic business strategy
- Integration will build trust and create value for a competitive advantage
- Cybersecurity is now a permanent capital expenditure and mandatory strategic investment - required to stay in business
- Business and technology leaders must work together to manage trade-offs
- Will require unbiased, independent third-party support to provide objective view and transcend internal “politics”
Practical corporate measuring tool
- “Cyber hygiene”
-
- Indicator of company performance
- Mirrors internal governance structure
- Outlines 3rd party stakeholder network
- Highlights IT maturity and employee productivity
- Exposes business borders (silos), friction and inefficiencies
- Cybersecurity assessment
-
- Due diligence for investments and M&A activities
- Measure PMI risk
- Prevents inheriting hidden and unknown cyber liabilities
Improved customer experience
Frictionless customer-security experience is now mandatory. Customers should be offered a secure and seamless digital experience.
- Security is now a Customer Experience (CX) priority
-
- Instills loyalty, confidence and trust
- Transparency, traceability, ethics, integrity, openness, accountability, competence and consistency on how customer data is collected and used
- Customer convenience requires better security (ie., storing credit cards so that customers don’t need to reenter)
- Achieve CX goals through effective cybersecurity
-
- Fewer complaints and calls
- Better ROI on marketing activities
- More sales
- Prediction of future trends
Counter Intuitive
Cloud storage
- Better protection than standalone server
- Better redundancy and resilience
- Consolidates surface area to manage / protect
Air gap
- Sensitive data confined to an unconnected system (but also unmonitored)
- Harder to monitor / detect for unauthorized activity
Too much security
- Actually increases risk
- Reduces efficiencies - i.e., Frequent phishing tests make employees overly cautious about opening / clicking anything
- Complacency - checklists don't equal protection
- False positives – Attackers intentionally trip alarms and send signals to draw away attention from primary objective
Backups
- Real time and insufficient depth may result in backing up (and overwriting with) damaged / faulty data
- Lack of testing results in finding out media is W/O (write only)
Blockchain
- No, it will not fix this problem today (yet)
Let us help you securely transform your organization
