Corporate Cybersecurity
- Every company is a technology company
- No company is immune from cyber attack – it WILL happen ("when" not "if")
-
No such thing as the term
“Cyber risk”today, it is just business risk - No organization is an island when it comes to data and cybersecurity

- Corporations are not prepared for the new risks
- Security is a people problem, not a technology problem
-
- Security solutions have technological components
-
- Presents a conceptual, organization, operational, technological, financial and management challenge
- Almost all security problems are due to blunders in design, implementation, operation or management
- Todays expanded cyber “surface area” magnifies even a single security incident
- Can result in unanticipated costs, operational shutdowns, reputational damage and legal consequences
- Result in physical destruction and loss of life
“There are only ‘two categories’ of companies affected by [cyber] trade secret theft – those that know they’ve been compromised
and those that don’t know yet.”
-Former Attorney General Eric Holder (February 20, 2013)
“Cyber is uncharted territory. It’s going to get worse, not better ...a very material risk that didn’t
exist 10 to 15 years ago.”
-Warren Buffett (Berkshire Hathaway 2018 Annual Shareholders Meeting)
Today's Cybersecurity Mindset

Today's organizations need to implement an
effective cybersecurity strategy
and to derive its multiple benefits
Risk and Maturity
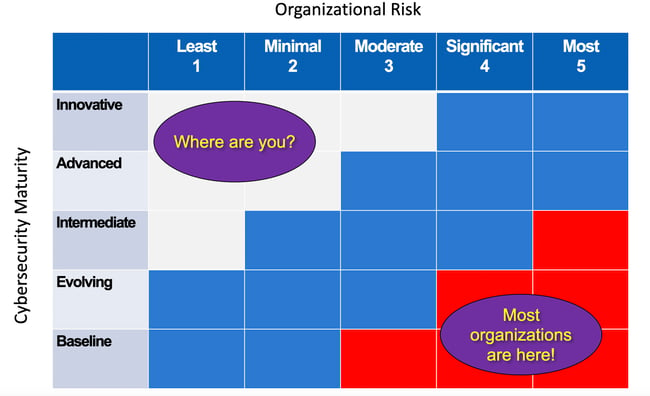
Too many areas to address alone...
- Architecture
- Asset management
- Awareness
- Business continuity management
- Data infrastructure
- Data protection
- Employees
- Governance and organization
- Host security
- Identity and access management
- Incident management
- IoT
- Metrics and reporting
- Network security
- Operations
- Policy and standards framework
- Privacy
- Security monitoring
- Software security
- Strategy
- Supply chain
- Third-party (and 4th party) stakeholder management
- Threat and vulnerability management
Follow the 7 P's
Proper
Planning and Preparation
Prevents
Piss Poor Performance
British Army adage
Let us help you change your mindset and effectively
plan, prepare and address cybersecurity
